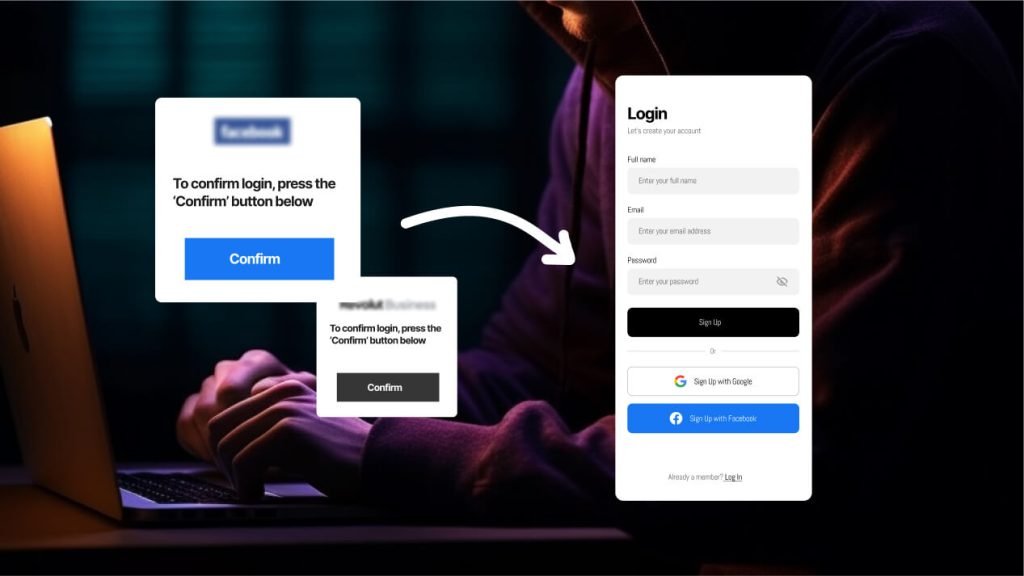
Yes, the world is changing hard right now! As we witness rapid advancements in artificial intelligence (AI), it is crucial to stay informed about the evolving landscape of cybersecurity. AI technologies have revolutionized various industries, including the realm of hacking and phishing. In the coming months, the world will experience significant transformations, making it imperative for individuals to understand the risks associated with AI-powered hacking methods and prioritize their online security.

AI has granted hackers access to powerful tools that can automate and enhance phishing attacks. From sophisticated email spoofing to the creation of hyper-realistic deepfake videos or voice recordings for social engineering, cybercriminals are leveraging AI to exploit unsuspecting individuals.
Whether you’re using services like Google, Facebook, Instagram, or WhatsApp, taking proactive steps to protect your passwords and accounts can save you from potential cyber threats.
The main Phishing techniques:
- Email Spoofing: Manipulating email headers to make an email appear as if it’s from a trusted source, deceiving recipients into sharing sensitive information or clicking on malicious links.
- Deceptive Websites: Creating fraudulent websites that mimic legitimate ones, tricking users into entering personal information or login credentials.
- Spear Phishing: Customized phishing attacks targeting specific individuals or organizations, using personalized information to increase the chances of success.
- Malicious Attachments: Sending emails with infected attachments that, when opened, can install malware or gain unauthorized access to a user’s system.
- Fake Login Pages: Creating fake login pages that imitate popular websites or services, aiming to capture users’ credentials when they try to log in.
- Social Engineering: Manipulating and exploiting human psychology to trick individuals into revealing confidential information or performing certain actions.
- CEO Fraud: Impersonating high-ranking executives within an organization to deceive employees into divulging sensitive data or initiating fraudulent transactions.
- Pharming Attacks: Redirecting users to fraudulent websites, often through DNS poisoning, with the goal of stealing personal information or login credentials.
- Smishing (SMS Phishing): Sending deceptive text messages that appear to be from trusted sources, tricking recipients into revealing personal information or clicking on malicious links.
- Vishing (Voice Phishing): Using phone calls to deceive individuals, often impersonating legitimate organizations or authorities, to extract sensitive information or initiate fraudulent actions.
Here are 10 protective measures to be attentive to when it comes to phishing attacks:
- Be Skeptical of Emails: Exercise caution when receiving emails, especially those requesting personal information, login credentials, or urgent action. Verify the legitimacy of the sender and scrutinize the email for any signs of phishing.
- Verify the Source: Double-check the email address or URL of any links provided in suspicious emails. Hover over the links (without clicking) to see if the URL matches the official website.
- Avoid Sharing Personal Information: Never provide personal information, such as passwords, Social Security numbers, or credit card details, through email or unfamiliar websites.
- Enable Two-Factor Authentication (2FA): Activate 2FA whenever possible to add an extra layer of security to your accounts. This helps protect against unauthorized access, even if your password is compromised.
- Educate Yourself: Stay informed about the latest phishing techniques and trends. Familiarize yourself with common phishing red flags, such as poor grammar, urgent requests, or unexpected attachments.
- Install Security Software: Use reputable antivirus and anti-malware software on your devices. Regularly update these programs to ensure they provide the latest protection against phishing attempts.
- Keep Software Updated: Keep your operating system, web browsers, and other software up to date with the latest security patches. These updates often include fixes for vulnerabilities that phishers may exploit.
- Use Strong, Unique Passwords: Create strong, unique passwords for all your online accounts. Avoid using the same password across multiple platforms to prevent widespread compromise if one account is breached.
- Regularly Monitor Accounts: Regularly review your account activity and statements for any suspicious or unauthorized transactions. Report any suspicious activity to the respective service provider immediately.
- Educate Yourself and Others: Share knowledge and resources about phishing attacks with friends, family, and colleagues. By collectively raising awareness, we can minimize the impact of phishing attempts and protect each other’s online security.
By following these protective measures, you can significantly reduce the risk of falling victim to phishing attacks and enhance your overall online security. Stay vigilant, be cautious, and never hesitate to report suspicious activities to the appropriate authorities.